It seems like a simple enough task. Use an Azure File share to store an executable and use a PowerShell script to execute the application on a new virtual machines. In practice, however, you might find that the executable is quietly failing to run. Running the executable on the server manually, the problem becomes apparent as a dialog box appears with the title:
“Open File – Security Warning”
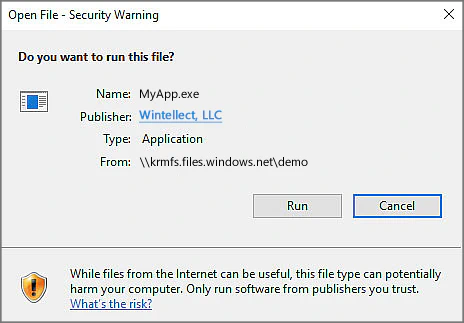
This issue typically occurs when executing files that originated from the internet. In this case, the cause is different: the UNC path is treated as part of the Internet Zone, restricting the permissions.
The workaround for this is to set the value of the SEE_MASK_NOZONECHECKSenvironment variable to 1. By configuring this value, processes in that environment will be allowed to execute without zone checking restrictions. Of course, setting this as a permanent value or at the system level is not recommended; that would disable all zone checking. Instead, we can configure the value as part of the PowerShell script.
1$env:SEE_MASK_NOZONECHECKS = 1When the script process ends, the value will be reverted. To revert it sooner, simply remove the value from the environment
1Remove-Item env:SEE_MASK_NOZONECHECKSWhere does this variable originate? It is a special value that allows ShellExecuteEx to bypass the zone checking put into place by IAttachmentExecute. The documentation on this is limited; it seems to have originated with Windows XP as part of a Microsoft Support article.
