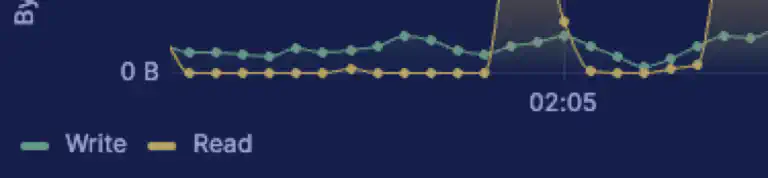
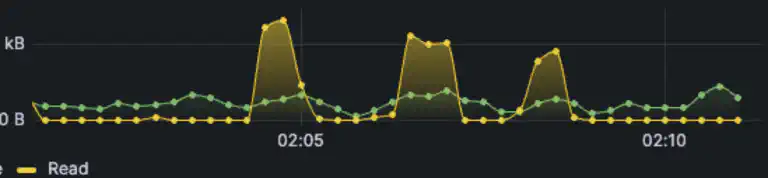
Part of mastering Kubernetes or containers is understanding how they work and how they interact with the host system. You’ve probably seen how to mount drives or folders into a containerized system, but there is another approach – mounting a file like a drive. This post will explore how to do this using a loop device in Linux.